id_tokens are sent to the client application as part of an OpenID Connect flow. They can be sent along side or instead of an access token, and are used by the client to authenticate the user. ID Tokens should be used to validate that a user is who they claim to be and get additional useful information about them - it shouldn't be used for authorization in place of an access token. The claims it provides can be used for UX inside your application, as keys in a database, and providing access to the client application.
id_tokens for a Microsoft identity are JWTs, meaning they consist of a header, payload, and signature portion. You can use the header and signature to verify the authenticity of the token, while the payload contains the information about the user requested by your client. Except where noted, all claims listed here appear in both v1.0 and v2.0 tokens.
The information about group and roles in the ID TOKEN is not mandatory. But in some use cases some application need to filter information on the client side using these information.
In order to make this information available in the roles & group claims we first need to specify them in the manifest.
Navigate to App Registration ->Select your application -> Click on Manifest
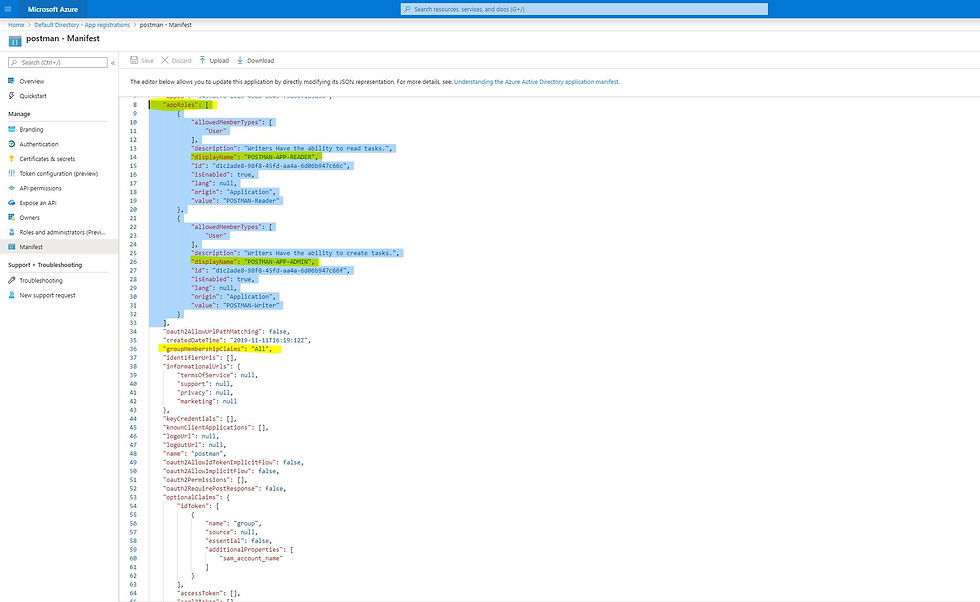
The application specific roles can be specified under the appRoles section. The id of the role should be unique. For example:
"appRoles": [ { "allowedMemberTypes": [ "User" ], "description": "Writers Have the ability to read tasks.", "displayName": "POSTMAN-APP-READER", "id": "d1c2ade8-98f8-45fd-aa4a-6d06b947c66c", "isEnabled": true, "lang": null, "origin": "Application", "value": "POSTMAN-Reader" }, { "allowedMemberTypes": [ "User" ], "description": "Writers Have the ability to create tasks.", "displayName": "POSTMAN-APP-ADMIN", "id": "d1c2ade8-98f8-45fd-aa4a-6d06b947c66f", "isEnabled": true, "lang": null, "origin": "Application", "value": "POSTMAN-Writer" } ]
Enabling the user groups visibility in the ID TOKENS can be enabled by adding this line:
"groupMembershipClaims": "All",
Now we have specified the roles and enabled the groups so we have to assign users to a group or assign a specific role to a user.
Navigate to: Default Directory -> Enterprise applications -> All applications
-> Postman -> Users and groups
Assign a user to your group and assign the roles above to the specific user. In AAD you can assign roles to a user or user group.
After this is done we could see the that the information is shown in the ID TOKEN as below:

Follow the following post if help is needed with setting up Postman:

Fashion trends come and go, but an anklet never goes out of style. This delicate piece of jewelry can bring a hint of anklet sparkle and charm to your look, whether you're wearing it barefoot on the beach or with sandals during summer.
Prana is a skincare brand that combines nature and science to create products that nourish the skin. Their commitment to prana natural ingredients sets them apart from many other brands in the market.
If you’re looking for an accessory to make your outfit pop is a fantastic choice. The shimmering metallic color silver purse adds a touch of glamour, especially when paired with darker or neutral tones. It’s a simple yet effective way to elevate your style and turn heads.
Drivers need to be particularly cautious when driving in windy conditions, as these vehicles are more likely to sway. Properly how long do gaming laptops last adjusting speed and being mindful of external conditions can help ensure a safer driving experience.
Renovating floors can dramatically change the feel of a home. If you're in the market for new materials, intafloors delivers options that are stylish practical, and long-lasting. With a focus on durability and design, you can count on finding the right flooring to complement any décor.